Axpert 11
TStructs (Forms)
- Create Form
- Create DC
- Create Fields
- Grid DC/frames
- Formulae in fields
- SQL in fields
- Drop down fields
- Autogenerate fields
- Table fields
- File upload fields in forms
- Photos &Image fields
- Barcode /QR Code Scanner
- Fill Grid
- Posting data – Gen maps
- Updating fields in DB tables – MD Map
- Toolbars in tstructs
- Tracking changes/Audit trial
- Try it yourself
IViews
Scripts
Axpert Jobs
Axpert Cards
HTML Plug-ins
Users & Roles
- Users, roles & responsibilities
- Responsibilities
- User Role
- User Login
- SSO Authentication
- Stay Sign In
Workflow
Axpert API
Application Var/Params
Publish Axpert Apps
Axpert Mobile
Settings
- Axpert installation
- Change password
- Forgot Password
- Developer Options
- Global Settings
- In-Memory DB
- Notifications for Long Running Webservice’s
- Axpert Configuration on web
- Axpert Licensing
Utilities
Customization
- Main Page Customization
- Home Page Customization
- More API
- Custom User Interface
For Reports - Custom HTML In Forms
- CSS And JS Customization
- Developer Notes
- Hooks In Forms
- Third Party SSO Integration
WebServices
Axfast
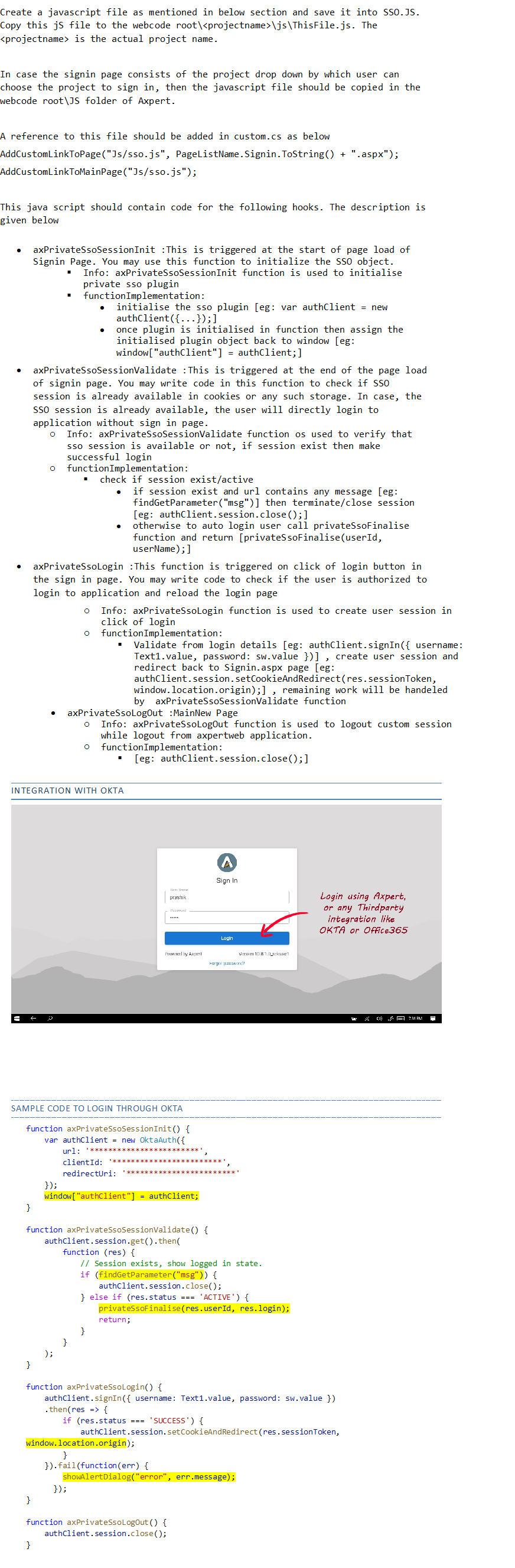
Third Party SSO Integration
SSO Integration through OKTA
SSO Integration through Azure AD
Steps to Enable SAML SSO:
- Add/Enable below web.config keys
- ServiceProvider and PartnerIdentityProviders needs to be changed in saml.config file
- ServiceProvider Name: Identifier (Entity ID)
- AssertionConsumerServiceUrl: Reply URL (Assertion Consumer Service URL
- PartnerIdentityProvider Name: Azure AD Identifier url
- SingleSignOnServiceUrl: Login URL from Azure AD portal
- SingleLogoutServiceUrl: Logout URL from Azure AD portal
- Certificate FileName: Certificate name has to be specified here. And the same can be downloaded from Azure AD portal. Copy this into Saml_Certificates folder in webcode
<add key="SamlPartnerIdP" value=""/ >
<add key="ssologin" value=""/>
<add key="ssoredirecturl" value=""/>
Example:
<add key="SamlPartnerIdP" value="https://sts.windows.net/0b1513a2-8f4d-4478-ab27-28da7a534984/"/>
[After this, add application in Azure AD portal. It will generate 'Azure AD Identifier' url that needs to be copied ]
<add key="ssologin" value="saml"/>
<add key="ssoredirecturl" value="http://demo.agile-labs.com/"/>